Wpa2 Can Generate Static Keys For Encryption
WPA encryption Key Generator
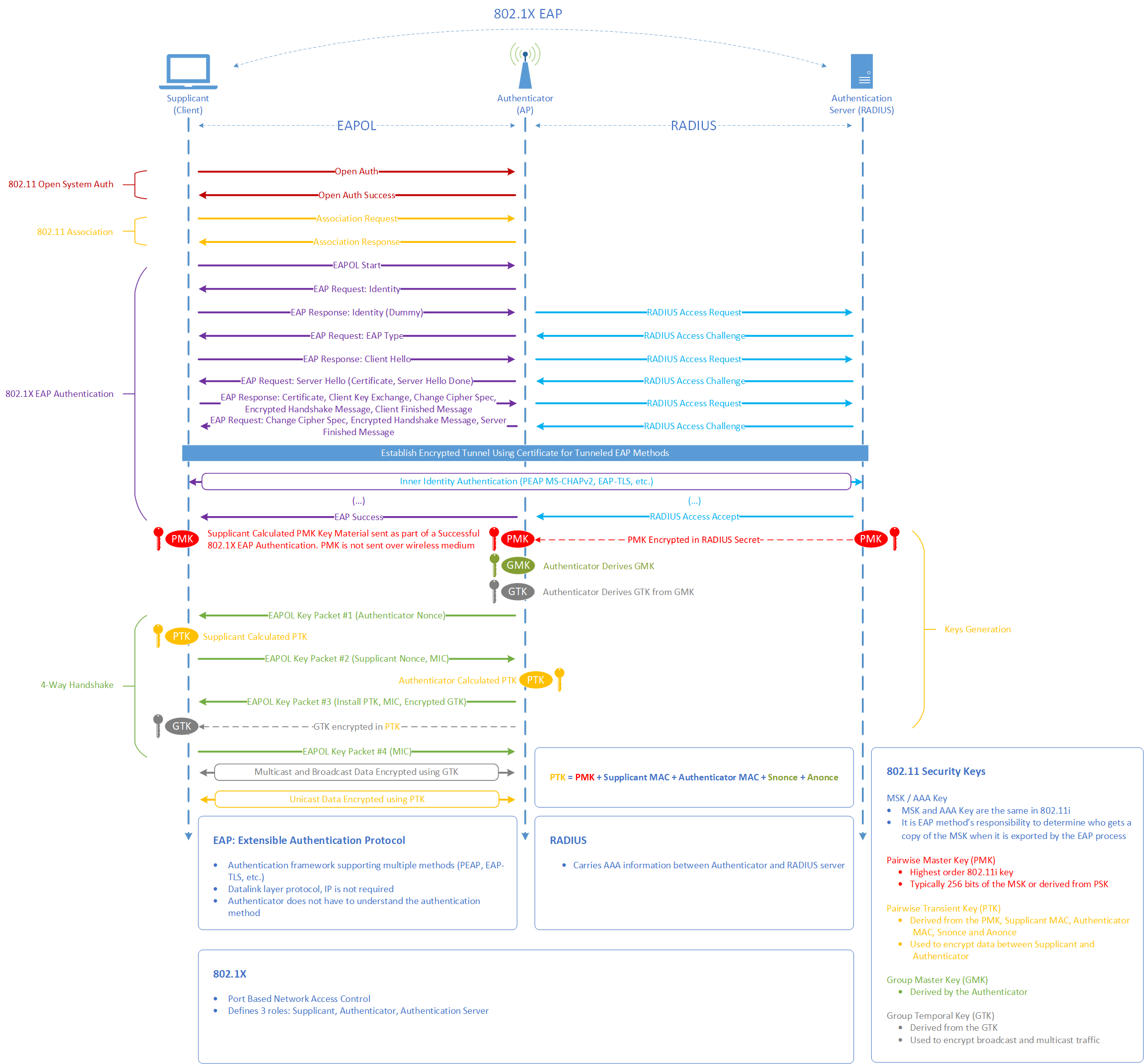
OKC roaming can be configured only for the Enterprise security level. Applicable to Enterprise and Personal security levels only. For the Open security level, no encryption settings are required. For Personal security level, select an encryption key from the Key management drop-down list. Paul has been hired as a consultant to secure the Levasseur Corporation's WLAN infrastructure. He has been asked to choose a solution that will both protect the company's. Equipment from theft and hopefully protect the access point's configuration interfaces from. Outside attackers. Sep 13, 2018 WPA2-Personal – PSK combines a passphrase (pre-shared key) and an SSID (which is used as a “seed” and is visible to everyone in range) to generate encryption keys. The generated key – a Pairwise Master key (PMK) – is used to encrypt data using TKIP/CCMP. This tool generate a WPA encryption key that you can use to secure your Wireless network. Generate the WPA Encryption key, copy it and paste it into your wireless router's configuration panel. Restart your DSL modem/router. Check the WEP Key generator. Wireless Security. Wired Equivalent Protocol (WEP) can be used to protect data as it is transmitted over the wireless network, but it provides no protection past the SonicWALL. It is designed to provide a minimal level of protection for transmitted data, and is not recommended for network deployments.
Create a WPA Key
This WPA Key Generator generate a WPA encryption key that you can use to secure your Wireless network. generate the WPA Encryption key, copy it and paste it into your wireless router's configuration panel. Restart your DSL modem/router.
Also check the WEP Key generator
Wi-Fi Protected Access
Wi-Fi Protected Access (WPA and WPA2) are systems to secure wireless (Wi-Fi) networks. They were created in response to several serious weaknesses researchers had found in the previous system, Wired Equivalent Privacy (WEP). WPA implements the majority of the IEEE802.11i standard, and was intended as an intermediate measure to take the place of WEP while 802.11i was prepared. WPA is designed to work with all wireless network interface cards, but not necessarily with first generation wireless access points. WPA2 implements the full standard, but will not work with some older network cards. Both provide good security, with two significant issues:
- either WPA or WPA2 must be enabled and chosen in preference to WEP. WEP is usually presented as the first security choice in most installation instructions.
- in the 'Personal' mode, the most likely choice for homes and small offices, a passphrase is required that, for full security, must be longer than the typical 6 to 8 character passwords users are taught to employ.
WPA is designed for use with an 802.1X authentication server, which distributes different keys to each user; however, it can also be used in a less secure 'pre-shared key' (PSK) mode, where every user is given the same passphrase. The Wi-Fi Alliance calls the pre-shared key version WPA-Personal or WPA2-Personal and the 802.1X authentication version WPA-Enterprise or WPA2-Enterprise.
Source: Wikipedia
WEP Key Generator
Contents
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document.
Use Cisco Feature Navigator to find information about platform support and Ciscosoftware image support. To access Cisco Feature Navigator, go tohttp://www.cisco.com/go/cfn. An account on Cisco.com is notrequired.
Prerequisites for Layer 2 Security
WLANs with the same SSID must have unique Layer 2 security policies so that clients can make a WLAN selection based on information advertised in beacon and probe responses. The available Layer 2 security policies are as follows:
- None (open WLAN)
- Static WEP or 802.1X
NoteBecause static WEP and 802.1X are both advertised by the same bit in beacon and probe responses, they cannot be differentiated by clients. Therefore, they cannot both be used by multiple WLANs with the same SSID.
- WPA/WPA2
NoteAlthough WPA and WPA2 cannot be used by multiple WLANs with the same SSID, you can configure two WLANs with the same SSID with WPA/TKIP with PSK and Wi-Fi Protected Access (WPA )/Temporal Key Integrity Protocol (TKIP) with 802.1X, or with WPA/TKIP with 802.1X or WPA/AES with 802.1X.
Information About AAA Override
The AAA Override option of a WLAN enables you to configure the WLAN for identity networking. It enables you to apply VLAN tagging, Quality of Service (QoS), and Access Control Lists (ACLs) to individual clients based on the returned RADIUS attributes from the AAA server.
How to Configure WLAN Security
Configuring Static WEP + 802.1X Layer 2 Security Parameters (CLI)
Before You BeginYou must have administrator privileges.
SUMMARY STEPS1.configureterminal
2.wlanprofile-name
3.securitystatic-wep-key{authentication {open sharedkey}encryption{10440}[ascii hex]{08}}wep-keywep-key-index1-4
4.end
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configureterminal Example: | Enters global configuration mode. |
| Step 2 | wlanprofile-name Example: | Enters the WLAN configuration submode. The profile-name is the profile name of the configured WLAN. |
| Step 3 | securitystatic-wep-key{authentication {open sharedkey}encryption{10440}[ascii hex]{08}}wep-keywep-key-index1-4 Example: | Configures static WEP security on a WLAN. The keywords and arguments are as follows:
|
| Step 4 | end Example: | Returns to privileged EXEC mode. Alternatively, you can also press Ctrl-Z to exit global configuration mode. |
Configuring Static WEP Layer 2 Security Parameters (CLI)
Before You BeginYou must have administrator privileges.
SUMMARY STEPS1.configureterminal
2.wlanprofile-name
3.securitystatic-wep-key[authentication {open shared} encryption{104 40}{asciihex}[08]]
4.end
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configureterminal Example: | Enters global configuration mode. |
| Step 2 | wlanprofile-name Example: | Enters the WLAN configuration submode. The profile-name is the profile name of the configured WLAN. |
| Step 3 | securitystatic-wep-key[authentication {open shared} encryption{104 40}{asciihex}[08]] Example: | The keywords are as follows:
|
| Step 4 | end Example: | Returns to privileged EXEC mode. Alternatively, you can also press Ctrl-Z to exit global configuration mode. |
Configuring WPA + WPA2 Layer 2 Security Parameters (CLI)
Before You BeginYou must have administrator privileges.
SUMMARY STEPS1.configureterminal
2.wlanprofile-name
3.securitywpa
4.securitywpawpa1
5.securitywpawpa1ciphers[aestkip]
6.securitywpawpa2
7.securitywpawpa2ciphers [aestkip]
8.end
Wpa2 Can Generate Static Keys For Encryption Windows 7
DETAILED STEPS| Command or Action | Purpose | |
|---|---|---|
| Step 1 | configureterminal Example: | Enters global configuration mode. |
| Step 2 | wlanprofile-name Example: | Enters the WLAN configuration submode. The profile-name is the profile name of the configured WLAN. |
| Step 3 | securitywpa Example: | Enables WPA. |
| Step 4 | securitywpawpa1 Example: | Enables WPA1. |
| Step 5 | securitywpawpa1ciphers[aestkip] Example: | Specifies the WPA1 cipher. Choose one of the following encryption types:
|
| Step 6 | securitywpawpa2 Example: | Enables WPA 2. |
| Step 7 | securitywpawpa2ciphers [aestkip] Example: | Configure WPA2 cipher. Choose one of the following encryption types:
|
| Step 8 | end Example: | Returns to privileged EXEC mode. Alternatively, you can also press Ctrl-Z to exit global configuration mode. |
Configuring 802.1X Layer 2 Security Parameters (CLI)
Before You BeginYou must have administrator privileges.
SUMMARY STEPSWhat Is My Wpa2 Key
1.configureterminal
2.wlanprofile-name
3.securitydot1x
4.security [authentication-listauth-list-nameencryption {010440}
5.end
DETAILED STEPS
| Command or Action | Purpose | |||
|---|---|---|---|---|
| Step 1 | configureterminal Example: | Enters global configuration mode. https://keensrus.weebly.com/blog/the-best-of-yarbrough-and-peoples-rarest. | ||
| Step 2 | wlanprofile-name Example: | Enters the WLAN configuration submode. The profile-name is the profile name of the configured WLAN. | ||
| Step 3 | securitydot1x Example: | Specifies 802.1X security. | ||
| Step 4 | security [authentication-listauth-list-nameencryption {010440} Example: | The keywords and arguments are as follows:
| ||
| Step 5 | end Example: | Returns to privileged EXEC mode. Alternatively, you can also press Ctrl-Z to exit global configuration mode. |
Configuring Layer 2 Parameters (GUI)
Before You Begin- You must have administrator privileges.

| Step 1 | Click Configuration > WLAN > . The WLANs page appears. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 2 | Click the WLANs profile of the WLAN you want to configure. The WLANs > Edit > page appears. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 3 | Click the Security > Layer 2 > tab.
To configure the WPA + WPA2 parameters, provide the following details:
To configure 802.1x parameters, provide the following details:
To specify Static WEP, configure the following parameters:
To configure Static WEP + 802.1X Parameters
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Step 4 | Click Apply. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Additional References
Related Documents
| Related Topic | Document Title |
|---|---|
WLAN command reference | WLAN Command Reference, Cisco IOS XE Release 3SE (Catalyst 3850 Switches) |
Security configuration guide | Security Configuration Guide (Catalyst 3850 Switches) |
Error Message Decoder
| Description | Link |
|---|---|
To help you research and resolve system error messages in this release, use the Error Message Decoder tool. |
MIBs
| MIB | MIBs Link |
|---|---|
| All supported MIBs for this release. | To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
Technical Assistance
| Description | Link |
|---|---|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
Feature Information about WLAN Layer 2 Security
| Feature Name | Release | Feature Information |
|---|---|---|
| WLAN Security functionality | Cisco IOS XE 3.2SE | This feature was introduced. |